Threat Intelligence
Smarter and Safer Than the Threats You Face
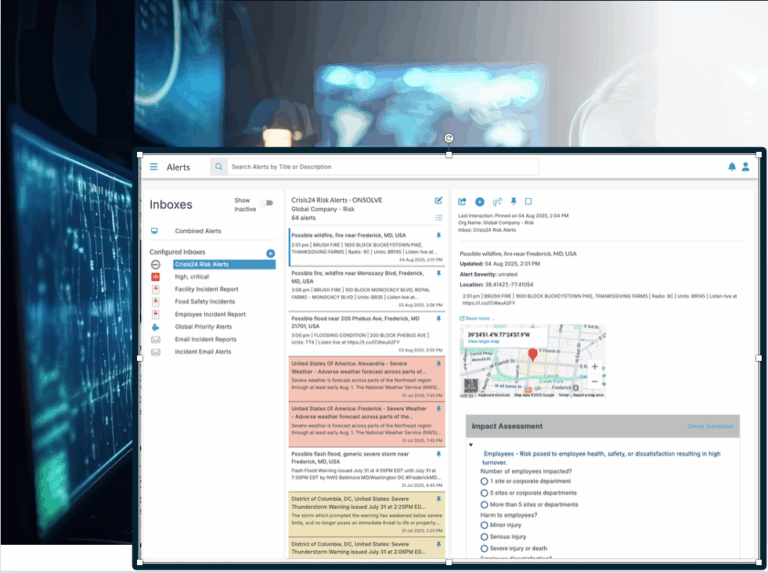
Use advanced threat intelligence with real-time insights into emerging risks and potential threats. Collect actionable intel from multiple sources to identify and respond to emerging threats quickly and effectively–minimizing impact during any crisis.
Threat Monitoring/Situational Awareness
Connect to trusted intelligence feeds to map and monitor threat levels in specified areas. Pull critical information from multiple sources to anticipate, assess, and act on potential threats.
Visual Dashboards
Track response status, monitor team updates, and follow a visual timeline in a centralized command center. Customize the command center to prioritize the tools and resources most critical to your response.
Historical Data Access
Conduct retrospective analysis, identifying patterns and recurring threats over time to uncover vulnerabilities, improve forecasting, and strengthen long-term risk mitigation strategies. Store a clear record of how threats were addressed for compliance, auditing, and post-incident evaluations.
Real-Time Alerts
Streamline incident detection and reporting with real-time alerts that immediately notify key personnel and automatically categorize incidents based on severity, impact, and urgency.
Threat Analysis
Transform raw data into actionable insights. Assess the credibility, relevance, and potential impact of each threat and identify patterns, track threat actors, and map behaviors against credible frameworks.
Data Collection and Aggregation
Using third party services, collect data from open sources (OSINT), dark web, social media, government feeds, commercial intel providers, etc. Monitor keywords, domains, and indicators of compromise (IOCs) in real-time. Connect with existing tools for streamlined data flow.
In Case of Crisis Is Used and Trusted by Many Leading Companies



Solutions
Stay one step ahead of emerging threats and disruptions.
Cybersecurity Threat Monitoring
Detect and respond to cyberattacks such as malware infections, phishing attempts, ransomware, and network intrusions. Continuous monitoring helps identify suspicious activities early, enabling IT teams to take action before sensitive data is compromised or operations are disrupted.
Physical Security Threats (Workplace Violence & Trespassing)
Track potential physical threats to facilities, including unauthorized access, trespassing, or early warning signs of workplace violence. Integrating surveillance systems, access controls, and behavioral threat assessments helps organizations respond swiftly to protect people and assets.
Social Media & Public Sentiment Monitoring
Monitor social media platforms and online forums for emerging threats such as negative campaigns, misinformation, or reputation-damaging content. Early detection enables proactive communication strategies to manage brand reputation and address crises before they escalate publicly.
Geopolitical and Civil Unrest Monitoring
Track political instability, protests, or civil unrest that could impact their workforce, facilities, or supply chains. Real-time situational awareness helps make informed decisions regarding travel advisories, site security, and employee safety.
Supply Chain Risk Monitoring
Monitor threats across their supply chain, including vendor disruptions, logistical bottlenecks, and regional risks like natural disasters or regulatory changes. Early alerts about supplier vulnerabilities allow businesses to adjust sourcing strategies and maintain operational continuity.
Environmental & Natural Disaster Monitoring
Receive real-time alerts for environmental hazards like earthquakes, floods, wildfires, or severe weather events. These insights enable organizations to activate emergency plans, protect facilities, and ensure the safety of employees and communities in affected regions.
