Build a Crisis Management Plan Using These 4 Key Steps

It is no secret that most businesses were unprepared for the pandemic. According to this study, only 62% of organizations have a crisis management plan to respond to any threat at all, not just a pandemic. And, of those companies that had a plan, very few organizations tested or updated them.
So, if you are one of the 38% without a crisis management plan, or are looking to optimize your current plans, here are some key steps to review.
Step 1 - Determine Your Distribution
Before you start writing a crisis management plan, it is important to first determine how you plan on distributing the information once completed. Depending on which method you choose will determine the template or format of how the plan should be written.
There are several ways plans can be disseminated, here is a reference that outlines several methods and highlights strengths and weaknesses for your consideration.
Step 2 - Core Crisis Management Protocols
The foundation of your crisis management plan are core protocols. These help you determine the level of risk each threat presents and the team and resources that will be deployed at each level.
A good starting point to determine the level of risk for each threat is creating a tiered approach. The lowest tier could be defined as an emerging issue with the potential to become a threat but currently has no mainstream media coverage, customer discourse, regulatory impact, etc. The highest tier could be defined as a significant threat that has wide visibility and is likely to impact the organization’s operations and reputation.
The plan can then be built on the threat levels that have been defined. Here are a couple of examples that the specific content should address:
- Who takes the lead responsibility for each level of threat (think location, function, department, team, etc.)?
- What is the system for reporting initial incidents?
- What is the escalation procedure at each level as an event becomes more threatening?
Step 3 - Tools to Support Decision Making
Now that you have identified your threat levels and escalation process in your crisis management plan, how do you plan on organizing the information? It is important to include easy-to-use guidelines, checklists and protocols that can easily be digested or deployed in the moment of a crisis.
|
Some examples of tools include:
|
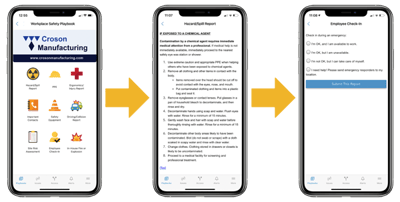 |
Step 4 - Specific-Based Scenario Plans
The next step is to take the crisis management protocols and tools to support them, and to apply it to specific threat scenarios.
Here are several common threats and why you should prepare for them:
-
Cyber-Security: With the pandemic, more people than ever are working remotely and according to this article, “A painful lesson executives, IT, and security teams learned during the pandemic last year was that they have to think of secure remote access as a business continuity issue as much as DDoS attacks, natural disasters, or nation-state attacks.”
-
Natural Disasters/Extreme Weather: Last year COVID threw a curve ball when it came to preparing for Hurricanes, wildfires and other extreme weather events. With the pandemic still around this, this whitepaper provides considerations of what to include in your plans this year to avoid the risk of infection.
-
Civil Unrest: Another threat that has become more common in recent years and according to this article, “there should be no expectation that 2021 will play out much differently.”
For more in-depth explanations, tips, examples of the above key steps, and seven additional scenarios you need to plan for, download our new guide ‘The Key Steps to Building a Crisis Plan.’
Learn how hundreds of organizations large and small are using our award-winning issue and crisis management platform, In Case of Crisis, to better prepare for and respond faster to emerging threats.








